Enter the Certificate Checking Tool!
More and more communications are becoming secured with certificates issued from a Public/Private Key Infrastructure.
The challenge is that certificates and more importantly, their expiry tends to not be tracked.
Why is this a problem? When a certificate expires and it’s not properly documented in the applications architecture, it’s really difficult to figure out where the problem is!
I wrote a Certificate Checking Tool in Python script to help track what certificate is issued to a server and return how much time left before the certificate expires.
This script will output the certificate metadata to stdout in regular format, or if specified, json format.
More information here on GitHub –> https://github.com/TheScriptGuy/certificateChecker
Additional Features
- Ability to upload results to a web server.
- Download a list of hostnames and ports to query or reference a file that has a list of hostnames and ports to query.
- For data aggregation purposes, you can tag the device performing the queries. For example – PROD, DEV, QA.
certCheck Help
$ python3 certCheck.py -h
usage: certCheck.py [-h] [--hostname HOSTNAME] [--displayCertificate]
[--displayCertificateJSON] [--displayScriptDataJSON]
[--displayTimeLeft] [--queryFile QUERYFILE]
[--uploadJsonData UPLOADJSONDATA] [--setTag SETTAG]
[--deleteTag] [--getTag] [--renewUuid] [--getUuid]
[--deleteUuid]
Certificate Checker V0.12
optional arguments:
-h, --help show this help message and exit
--hostname HOSTNAME Hostname to get certificate from. Defaults to
google.com
--displayCertificate Display certificate info
--displayCertificateJSON
Display certificate info in JSON format
--displayScriptDataJSON
Display script info and queried certificates in JSON
format
--displayTimeLeft Display time left until expiry on certificate.
--queryFile QUERYFILE
Import a query file to for hostname queries. Supports
local files and HTTP/HTTPS links
--uploadJsonData UPLOADJSONDATA
Upload JSON data to HTTP URL via HTTP POST method.
--setTag SETTAG Set the tag for the query results. Creates tag.cfg
file with tag.
--deleteTag Delete the tag file - tag.cfg
--getTag Get the tag from tag.cfg file
--renewUuid Renew the UUID value.
--getUuid Get the UUID value from uuid.cfg file.
--deleteUuid Remove the UUID value. Caution: when script runs again
a new UUID will be generated.
Example 1
The :443 is optional. The script by default attempts on port 443. If your website is on a different port, just specify a different port after the colon.
$ python3 certCheck.py --hostname apple.com:443 --displayTimeLeft
1 year, 18 days, 7 hours, 23 minutes, 16 seconds
Example Output

Example 2
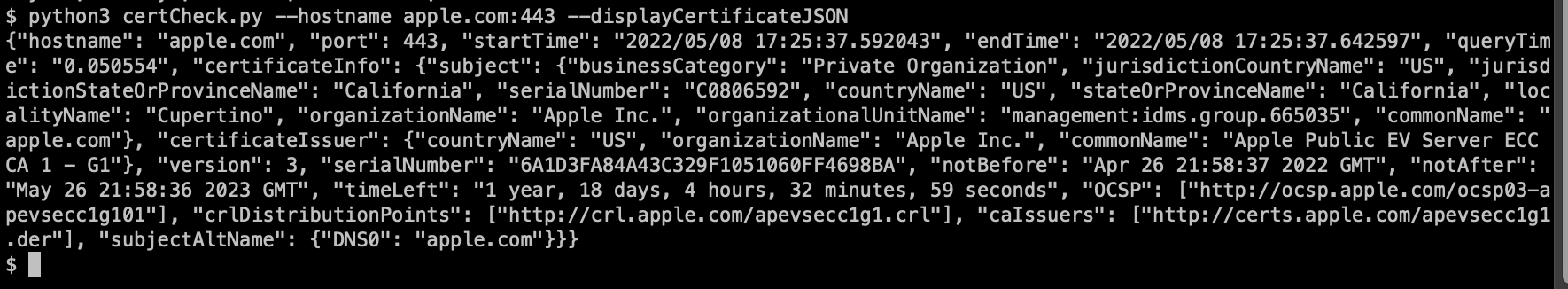
To display certificate metadata in json format, try this:
$ python3 certCheck.py --hostname apple.com:443 --displayCertificateJSON
{
"hostname": "apple.com",
"port": 443,
"startTime": "2022/05/08 14:38:55.216332",
"endTime": "2022/05/08 14:38:55.267096",
"queryTime": "0.050764",
"certificateInfo":
{
"subject":
{
"businessCategory": "Private Organization",
"jurisdictionCountryName": "US",
"jurisdictionStateOrProvinceName": "California",
"serialNumber": "C0806592",
"countryName": "US",
"stateOrProvinceName": "California",
"localityName": "Cupertino",
"organizationName": "Apple Inc.",
"organizationalUnitName": "management:idms.group.665035",
"commonName": "apple.com"
},
"certificateIssuer":
{
"countryName": "US",
"organizationName": "Apple Inc.",
"commonName": "Apple Public EV Server ECC CA 1 - G1"
},
"version": 3,
"serialNumber": "6A1D3FA84A43C329F1051060FF4698BA",
"notBefore": "Apr 26 21:58:37 2022 GMT",
"notAfter": "May 26 21:58:36 2023 GMT",
"timeLeft": "1 year, 18 days, 7 hours, 19 minutes, 41 seconds",
"OCSP":
[
"http://ocsp.apple.com/ocsp03-apevsecc1g101"
],
"crlDistributionPoints":
[
"http://crl.apple.com/apevsecc1g1.crl"
],
"caIssuers":
[
"http://certs.apple.com/apevsecc1g1.der"
],
"subjectAltName":
{
"DNS0": "apple.com"
}
}
}
Example output: